Abstract: This paper introduces the basis of the built-in ATM network system of Daya Bay Power Station, and achieves resource sharing with Ling Ao Nuclear Power Station, and fully obtains the information resources on the Internet. Based on a series of related technical analysis and demonstration, it analyzes and compares several The technical solution has successfully solved the two contradictory problems of network security of the Internet, successfully implementing the best solutions.
1.1 LAN Foundation The Daya Bay Nuclear Power Station ("Nuclear") network system has undergone nearly 10 years of construction. It has evolved from a stand-alone microcomputer and a single IBM mainframe system to the current set of mainframes, minicomputers, PC servers, and PCs. Multi-platform, such as a machine, is a network system with network computing as the center and more than 40 application systems running on different platforms. The system covers 18 buildings including the 01th floor, BX building, and BA building within a 5km range. Structured wiring is used inside the connection, and a Category 5 twisted pair cable capable of supporting 155Mbit/s is used. The IBM8271 is used as the endpoint device of the ATM backbone network in each building. It is connected to the 155M backbone network, and 8 or 16 unique 10Mbit/s ports are connected. It can connect to the departmental Ethernet segment, LAN server or IBM8224HUB, under a HUB. There are 16 ports sharing 10 Mbit/s, and 16 workstations can be connected. Two IBM 8260 multi-protocol intelligent switches were placed on the 01th floor and the BX floor, and one RS/6000-41T was equipped with IBM Netview for AIX software as a network management device.
The Ling Ao Nuclear Power Plant (2nd Core), which is 2km away from Daya Bay Nuclear Power Station, also uses ATM technology as a backbone network to build a management computer network. The network uses two BAY5aDOBH and one BAYCl00 as the main switching equipment. BAY28115 and BAYC50 are installed in each wiring room. Through the integrated wiring system of the LBX/LBA building, the user workstation is directly connected or the user workstation is connected through the BAY28113HUB. The network mainly covers the LBX/LBA building, and it also covers some of the office areas on the site and on the 01th floor.
1.2 The issue of networking problems With the continuous development of a nuclear computer application system, computer systems play an increasingly important role in production, maintenance, administration, finance, personnel, etc., CBA (Computer Aided Isolation System), More than 40 applications such as WPMS (Work Process Control System) and AMS (Administrative Management System) are gradually becoming huge productivity resources. With the advancing of the construction of the dual-nuclear engineering project and the beginning of production preparation, a number of application systems, such as the Transfer and Operation Control System (TCS) and the program database system, have become resources that must be shared by one nuclear and two nuclear resources. One or two cores need to run the same software on different servers or directly share the same server and the same software. The amount of information exchanged between the first and second cores is very large. Therefore, the guiding ideology of “one site, multiple reactors, group reactor management,†and “one or two nuclear shared resources†requires that one core and two cores must interconnect computer networks as soon as possible. In addition, the rapid development of the Internet has provided a large and abundant information resource for the production and operation management of the Daya Bay Nuclear Power Station and the construction and management of the Lingao Nuclear Power Station. Whether these resources can be fully and effectively used has become an urgent issue to be resolved. One and two independent LAN systems urgently need to be linked to the Internet.
While the Internet has brought great economic benefits, the importance of network security is particularly prominent. 1. Interconnection between the two core networks requires that the production operation of the single core and the construction of the second core do not interfere with each other, and the interconnection of the nuclear power grid and the Internet requires that the safety of the nuclear power grid itself be guaranteed. Therefore, the interconnection of the first and second nuclear networks and the interconnection between the first and second cores and the international network must address security issues.
2 Networking Schemes 2.1 Analysis of the Interconnection Scheme of the First and Second Core Networks 2.1.1 Networking Principles (1) A core of existing IBM equipment is connected to the newly purchased BAY equipment of the second core. As early as the second core to determine its network program, the issue of the interconnection of the first and second nuclear networks has been proposed. Obviously, if IBM's products are used in the two-core network, the networking is technically very simple. However, considering comprehensive considerations, the two-core network still uses BAY products. Therefore, the work of network interconnection must be based on objective reality. It is necessary to connect IBM equipment and BAY equipment. (2) The network interconnection bandwidth must reach 100 Mbit/s. According to the forecast of the information flow involved in the application system, the network interconnection bandwidth will eventually reach 100 Mbit/s, but the initial bandwidth requirement of the network may be appropriately reduced. (3) After the network is interconnected, the management of division of labor of the first and second nuclear networks. Considering that a nuclear network is mainly used for production and operation, the second-nuclear network is mainly used for engineering construction at this stage. The requirements for security, stability, and real-time of the two networks are not exactly the same, and the first and second nuclear networks are different. Cost centers, financial separation, and equipment management and asset management, separate management are more appropriate. (4) The disruption of a nuclear network cannot be caused during the process of network interconnection. Since a nuclear network is in a real-time production running state, network interruption will have a large impact on production operations. Therefore, a nuclear network cannot be interrupted under normal circumstances. However, in the process of network interconnection, some tests require that the network system must be stopped. In this case, only perfect the plan as much as possible, reduce the number of downtimes, and reduce downtime, especially when making changes to the network, so as to avoid network damage caused by networked tests. (5) Network interconnection with the lowest possible investment. On the basis of ensuring the effective implementation of various functions of the network interconnection, as far as possible, simple solutions and cheap equipment are used to reduce investment costs.
2.1.2 Analysis of major tests (1) Di-nuclear network. Server: The existing server Lanpc-S7, share resources Proj98, configure the corresponding IP, gateway, WINS and other parameters; workstation: Use a laptop, configure the appropriate IP, gateway, WINS and other parameters; Gateway: use 1 SUNNltra1 machine, install the Solaris operating system and Firewall - 1 for Solaris firewall software, set up multiple network cards, configure the appropriate parameters.
(2) Simulation of a nuclear network. Install an NT server LLC, install the WINS service, share the resource test, and configure the corresponding gateway parameters. Workstation: Use a laptop and configure the corresponding IP, gateway, and WINS parameters. The network connection is shown in Figure 1.
On the second-core workstation, first log in to the second-core network with the second-nuclear network ID, Telnet to the firewall, perform user authentication, exit Windows after the login, and log in to the core network with a nuclear network ID, and then map. And use a core of server resources.
On a nuclear workstation, first use a nuclear network ID to log in to a core network, Telnet to the firewall, perform user authentication, and then log out of Windows and log in to the second core network with the second core network ID. Then, the user can be mapped. And use the dual-core server resources.
2.1.3 Basic scheme Similar to the above scheme, through the experimentation and analysis of multi-platform and multi-firewall software, in order to make full use of the resources of one or two cores and save their own investment, and taking into account future functional expansion and development, The one-core network side sets up routers and firewalls, while the two-core network uses the original routing devices and firewalls as peer routers and firewalls, as shown in Figure 2.
2.2 Implementation of the First and Second-Core Network Interconnection Scheme 2.2.1 Server Hardware Configuration SUNU1tra2 Machine: 100M Ethernet port, 2x200MHz CPU, 21-inch display, 256MB RAM, 4GB hard disk, keyboard, 10/100M adaptive Ethernet card; SUNC12for Ultra2/ E2; 3-inch floppy disk drive; tape drive.
2.2.2 server software configuration SUNSolarisServer2.6 Chinese Enterprise Edition; SUNSolsticeFirewall-13.Ob firewall software, unlimited users.
2.2.3 Server Debugging Process The installation and configuration of SUN SolarisServer 2.6 system software; the installation and configuration of SUNSolarisFirewall-13.0b software; the setting of parameters in the application of SUNSolarisFirewall-13.0b; the setting of parameters in the application of SUNSolarisFirewall-13.Ob is divided into three parts: (1) Define Workstation and Network Objects. (2) Create users and groups. (3) establish a rule, the main purpose of the rule is as follows: for any user in a two-core network, allow access to a nuclear network resource (JVC) after verification from a nuclear firewall on any machine of the second-core network. LAN segment); For any user in a nuclear network, any machine from a nuclear network (ie any machine in the JVC-LAN segment) is allowed to pass the verification without a nuclear firewall (but verified by a second-core firewall). ), access to the dual-core network resources; in addition, refusal to exchange visits between any users of the first and second cores and any machines.
2.2.4 Configuration of the Client Side The configuration of the client side of the core; configuration of the Client side of the second core.
2.2.5 Configuration of Static Routes on the Network There are five ELANs configured in the existing one-core ATM network switch, and dynamic routing is adopted between each ELAN. Default Gateway 10.1.3.1 is configured and assigned to the DefaultGateway through the DHCP server. The Client side enables automatic routing and mutual access between machines on the entire network. However, the first and second nuclear network segments are different, and routing problems exist when they are connected. To solve this problem, there are two methods: (1) Manually set static routes on each server and client. This method has a heavy workload, and static routes must be set for each new server or shared resource, which is inconvenient and impractical. (2) Set static routes in the MSS on the ATM network switch. This method Client does not need to change, transparent to the user, but to change the MSS configuration, ATM network switches must be shut down to set; the advantage is transparent to the user, and once and for all. Based on everything for the user, without increasing the workload of the user, making the user easy to use, and being transparent to the user, it is also considered that the change to the MSS configuration is a one-time behavior and does not need to be changed later, so the second method is adopted.
2.2.6 Logging in to the other party's network Steps: Step 1: Log in to the second core network. Step 2: Log in to the second core network.
2.3 Analysis of interconnection schemes between nuclear power grids and international networks 2.3.1 Networking mode selection How enterprises choose the right network access mode and the appropriate ISP according to their own actual situation are the primary issues faced by companies accessing the Internet. Internet access can generally use single-machine dialing, ISDN, ADSL, DDN, etc. The DDN mode is suitable for a certain scale of network systems such as routers, hubs, servers, and workstations, and can be used to publish Web sites, suitable for large-scale enterprises or information services. Business. The original 13 single-line dial-up accounts for the Daya Bay Nuclear Power Station, but the company has hundreds of network users need to access the Internet. Hundreds of stand-alone users access the Internet, which will be very complicated in management. Therefore, from the analysis of transmission rate and cost balance, the management will be very complicated. Therefore, from the analysis of transmission rate and cost balance, consider web publishing and management. The Daya Bay nuclear power plant decided to use the DDN private line method to access the Internet.
2.3.2 Selection of network export points Since Daya Bay Nuclear Power Station is located in Dapeng Town in the outskirts of Shenzhen and is 70km away from the urban area, Renren Exit Point has two options: First, take the Great Wall Tower in the Central District of Shenzhen City as the exit point. The communication line between Great Wall Tower and Daya Bay and the G.703 interface at both ends of the line. The routers were set up in the downtown area and Daya Bay. The network equipment and servers were installed in Daya Bay. Outside the Great Wall Tower, Shenzhen City's Data and Communications Bureau used a special line to pick up Chinanet. Second, take the Dapeng Town Post Office as the exit point, and use Dayeng Bay to use the line of the post office of Dapeng Township to join Chinanet. The previous solution has a high level of network access, is less affected by routing, and has stable lines. It does not require construction. The interface can be reserved with the Guangdong Nuclear Power Group Company located in Shenzhen City. However, the investment for a router needs to be increased, and the workload is relatively large. The latter plan has relatively less workload and simple technology, but it has a low level of network access and is affected greatly by routes. The Dapeng branch has a relatively low level of technical and service personnel, and the line is unstable. Construction problems may exist. Through the above-mentioned advantages and disadvantages, Daya Bay Nuclear Power Station chose Great Wall Building as the exit point of the Internet special line.
2.3.3 Firewall Selection Effectively protect the internal network security of the company and allow internal users to efficiently access the Internet resources. This is a standard requirement of the firewall. When choosing, there are three factors to consider: safety, stability, and high performance.
As far as Cisco PIX Firewall is concerned, it is a hardware-based dedicated firewall that effectively hides internal network addresses. It only has one or several virtual addresses externally, and true hosts and users do NAT (Network Address Translation) or PAT. (Port address translation), completely hidden, with high security. In addition, the control microcode used by the PIX is different from the source code of the software firewall and is not easily available to hackers, thereby further improving the security. PIXFirewall's security algorithms are also special. CPU-based firewalls based on Unix or other operating systems process a large number of packets at the application layer. PIXFirewall uses secure real-time embedded systems at the network level and below. Process the data.
PIX's high performance also benefits from its pass-through proxy feature. Once external access is verified to meet the requirements of the control system, it converts the conversation flow so that the traffic flows directly between the two parties. This speeds up the operation and greatly reduces the number of ordinary firewalls. The amount of resources spent on user authentication. Due to the hardware-based architecture, the execution speed is extremely fast and throughput is high. At full load, the operating speed exceeds 45 Mbit/s, supports T3 speed, and can support up to 16000 TCP sessions at the same time. This performance is based on Unix firewalls. Several times. Simple configuration management is also a highlight of the PIX. Once configured, it does not require frequent maintenance. In this system, 3 network card configurations are used to enhance security and flexibility. The WebServer and MailServer that are traditionally placed on an external network are also placed under the protection of the Firewall (ie, the DMZ zone), leaving ample room for security for future high-security applications such as e-commerce applications. Therefore, Daya Bay Nuclear Power Station chose the hardware firewall PIXFirewall as the Internet firewall.
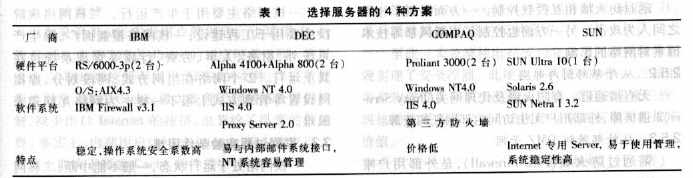
2.3.4 Server Selection The server is the core of the system. Whether the server hardware and software can be correctly selected and successfully installed is the basis for the success of the entire system; whether or not they can be effectively used after successfully installing the server hardware and software is the guarantee of the system operating efficiency. . The choice of server generally considers reliability, security, and processing power. With regard to the specific choice of servers, four sets of solutions have been designed, as listed in Table 1 below. In the above 4 sets of solutions, the solution of SUN server plus Cisco PIXFirewall has many advantages. The combination of SUNUltra hardware platform and Netra Internet software is a solution specifically designed to solve the Intemet networking problem. This solution has stronger functions in terms of hardware structure, reliability, scalability, and is applicable to larger enterprises. Therefore, in the selection of servers, the SUNAtra server is used in the Daya Bay nuclear power plant Intemet system.
2.3.5 Client hardware and software selection The hardware directly utilizes various types of PCs already on the Daya Bay nuclear power plant network. The client software also directly utilizes the existing Chinese Windows 95. This will save investment on the one hand and the other on the other. Department users can use Intemet on the basis of the original software and hardware, reducing the workload of user training and software installation, and users will feel simple and easy to use.
2.3.6 Router Selection There are two routers in the Internet access line of Daya Bay Nuclear Power Station, namely No. 16 Building of Great Wall Tower in Shenzhen and 01th Floor of Daya Bay Nuclear Power Station. Combined with the existing network conditions of Daya Bay Nuclear Power Station, there are two types of routers to choose from, one is the IBM2210 router and the other is the Cisc04500 router. Other brands and models of routers have no special advantages. In comparison, IBM2210 and Cisco4500 have a wider range of features and options, are cheaper, and have a higher utilization rate in Internet node connections, facilitating technical support. In particular, the Cisc04500 system software image is compressed and stored in flash memory. Memory is more reliable than disk and is easy to develop and maintain. Therefore, Cisc04500 was selected in the Internet access plan of Daya Bay Nuclear Power Station.
2.4 Interconnection Scheme of Nuclear Power Grid and International Network Implementation 2.4.1 Basic functions Establish a 128K DDN dedicated line and connect the Internet system of the nuclear power plant to the Chinanet backbone network through a dedicated line. This DDN private line supports most of the protocols based on Internet. The standard Internet service for internal users, including Web browsing, FTP, Telnet, and E-mail services based on POP3/SMTP. Open the company's Web site to external users. The system can also provide BBS, directory services, etc. With the deepening of Internet applications, new services will be added to the system.
2.4.2 System Configuration Functions (1) SUN server. Configuration: SunUltra10Server, CPU300MHzUltraSvarc, hard disk 4.3G, 128M memory, 24xCDROM, 1.44M, floppy drive, 10M/100MEthernet network card, 512KCache, based on Solaris2.6 Chinese operating system, running Netral3.2 groupware; function: WebServer is Netra13.2 group Bundled Netscape Enterprise Server 3.0; E-mail service: provided by Sendmail, is a built-in component of the operating system; DNS service: BIND, is an international popular Unix-based universal freeware; BBS service: shareware, downloaded from Internet.
(2) Backup DNS server. Configuration: 1 PCServer based on NTServer4.0; Function: As a backup of the primary DNS, it works in the case of a failure of the primary DNS (such as a down machine) to resolve the company's domain name.
(3) Proxy server. Configuration: PCServer, dual SCSI hard disk, based on NTServer4.0, running MSProxyServer2.0; features: (0 as a proxy for users to access the Internet, including WebProxy and WinsockProxy, where WebProxy implements HTYP, n7, Gopher, SSL, and other browser protocols, and With the local cache Cache configured, Winsock Proxy opens other protocols, including the POP3/SMTP mail protocol, acting as a proxy for the post office so that Winsock clients can communicate transparently with the mail server.2 User Management: Proxy Server is responsible for user authentication, traffic Monitoring, user accounting and other management tasks.
(4) PIXFirewall. Configuration: Cisco's professional hardware firewall, with three 10/100M adaptive Ethernet cards, 1024 simultaneous session licenses, configuration information is written to the built-in FlashMemory; Features: PIXFirewall firewall provides network-level security protection as The system separates the security gateways of the internal and external networks and the DMZ (public security zone) network segment, and hides the internal network through address mapping to prevent hackers from attacking the intranet. Configure the necessary protocol pipes (WWW, DNS, etc.) for external users.
(5) Router. Configuration: 2 Cisco 4500 modular routers, one of which is equipped with a 4-port G. 703 modules and one dual serial port module, and another one is equipped with a 4-port G. 703 modules and a dual Ethernet module; Function: Cisc04500 is Cisco's high-end products that support E1 (T1) line connections. In this system, in addition to the standard network route, the router 4500 has one important application: using G. The 703 module realizes 2M bandwidth communication between Shenzhen Great Wall Tower and Daya Bay, and can achieve hot backup of fiber/microwave communication.
(6) DTU. The NewBridge2603 synchronous data transmission unit is connected to the DDN network node at the opposite end of the data post office to realize synchronous communication of Internet information data.
(7) Hub. 3comOfficeConneet intelligent hub, light and simple, used for network segment expansion and device-to-terminal signal relay.
2.5 Security Strategies for Nuclear Power Networks 2.5.1 One- and two-core networks use mutual authorization control between firewalls to limit human-to-human interactions on the one hand; on the other hand, they also control technical factors such as broadcast storms on networks. influences.
2.5.2 There is no direct channel from the external network to the intranet. There are firewall and ProxyServer 2 barriers, and external users cannot access any resources on the intranet.
2.5.3 From the external network to the DMZ Subnet The firewall (PIX/Firewall) is required. It is the only network segment accessible to external users. The company's Internet host, SunServer, is on the DMZ subnet. The firewall performs strict security settings: the DMZ subnet uses the reservation IP address of the Internet, and an address mapping pipe is established between the external network and the DMZ. The external user accesses only the mapped IP address of the host on the DMZ, and does not know the real IP address. Can not be directly accessed, thus achieving IP address translation and shielding, effectively preventing IP fraud and other hackers commonly used tactics.
2.5.4 There are two barriers from the DMZ to the intranet with firewalls and proxy gateways. There is no direct pipeline.
2.5.6 From the Internal Network to the Extranet Through the PIX/Firewall/proxy, you can transparently access Internet resources (connected to the opened service). After proper configuration of the gateway and the PIX, various external access services can be carefully adjusted, all IP packets can be filtered, and all access information can be monitored.
2.5.7 From the Internal Network to the DMZ
Open protocols such as HTTP, Telnet, and POP allow authorized users to access this network segment transparently.
2.5.8 From the DMZ to the external network Through the firewall, the external network can be transparently accessed.
The above strategies are mainly set for the direct invasion of external hackers, but hackers can also use indirect means to attack, mainly: mail delivery and internal users to download infected files, which is already within the scope of the virus. Currently on the intranet, with the exception of Unix hosts, software for real-time monitoring of viruses (Cheyenne AntiVirus for CA) can effectively monitor the delivery and execution of files. In theory, it can prevent the spread of infected files. With the development of network technologies, the security strategy of nuclear power networks is also constantly improving. Connection between different ATMs in a two-core backbone network Although ATM technology has developed over the past few years, its stability, security, and manageability have been strong, but there are still problems with complex architecture and inconsistent agreements among vendors. Difficulty in connecting ATMs from IBM to BAY.
3.2 First and second nucleuses 2 Different management methods of the network One nuclear network is mainly used for production and operation. The second-nuclear network is mainly used for engineering construction at this stage. The one-nuclear network covers a wide range, except for the production system, finance, personnel, Management systems, such as labor and capital management, are also running on it. The two networks have very different management methods, such as networking methods, network segmentation, and virtual network settings, which create difficulties for network interconnection.
3.3 Networking process Experimental conditions Difficulties A nuclear network is in operation and cannot be interrupted. A dual-core network does not have a complete physical environment, and networked devices cannot be purchased before the actual solution is determined. Therefore, they must be simulated first. Conduct networking experiments and make theoretical projections, then research, select, determine networking solutions, and purchase related equipment. This kind of process is more difficult and risky for the initial experiment.
3.4 Long-distance communication between nuclear power grid and international network In this system, the access point of the Internet is in the Great Wall Building of Shenzhen City, and the servers and company users are all in Daya Bay, and the distance between them is 70km. How to reliably cross this distance and effectively transmit information is a challenging issue. The system uses two Cisco 4500 routers as the end devices, using fiber optics and microwave access to solve this problem.
The Cisco 4500 is a modular router that integrates 4 2M (E1) ports on its standard G.703 module and provides up to 8M of bandwidth at the same time. Connecting two E1 lines can be set as hot backup. When one channel fails, it can be automatically switched to the other. When there is no fault, two E1 lines are transmitted concurrently. This feature is used to achieve hot backup of the fiber/microwave. In communication debugging, the initial discovery error rate is as high as 40%. After searching for reasons by multiple parties, after resetting the Timeout value and related parameters, the code rate is reduced to a few PPM (parts per million), and the transmission quality is better than Intemet signal quality requirements for transmission channels.
3.5 Nuclear Power Grid User Management and WebCache (Cache)
3.5.1 Stable and reliable user authentication, logging, and traffic statistics are important aspects of network management. Initially, PIX-based ACS authentication was used, but failed to achieve the desired goal. Later, it adopted a proxy server and carefully configured it. Performance adjustment satisfactorily solved the complex requirements put forward for network management and achieved: (1) stable security verification, user authorization, and resolution of the problem of unified coordination with the main domain of the company's internal network, ie, one login, one verification, and transparency Use authorized services. (2) More detailed monitoring functions, including system performance monitor and real-time user status monitoring. (3) User log, log content includes: user ID, login time, information flow, service type, access to resources, etc., and can lead to a database for easy management.
3.5.2 Establishing a Local Cache is the Key to Improving User Response Performance After implementing user management with Proxy, Proxy Cache is also used to increase the Proxy's corresponding hard disk space. It can actively and periodically cache files that users have accessed to ensure the availability of data. Through Cache, the control over network resources has been greatly improved, the congestion of exported Internet has been reduced, and expensive information fees have also been saved. In fact, the speed of Internet access by internal users depends largely on the performance of the high-speed cache.
3.6 Client Configuration 3.6.1 About defaultgateway The company intranet has multiple subnets: 10.1.xx, 10.2.xx, 10.3.xx, etc. To enable users of different network segments to achieve smooth resource sharing, you must set The correct defaultgateway. In the initial implementation of the solution, the PIX internal Ethernet interface company 10.1.XX network segment, the user to access the Internet through the PIX, the default gateway must point to the PIX's internal Ethernet interface, but users of other network segments will not be able to access the Internet. To do this, first set up a static route on the IBM 8260 Switch (smart switch on the backbone) and point the Internet gateway to this PIX port. However, it has a great impact on the stable operation of the company's backbone network, and some of the company's online applications are 24 hours without interruption. Therefore, it adopts a proxy service mode to set up a proxy gateway at the user's end to ensure no change to the existing intranet. Next, this routing problem is better implemented.
3.6.2 Internal User Access to the Corporate External Home Page The corporate home page is located on the DMZ network segment (1P: 192.168.xx) and is independent of the external Internet and intranet. Internal users cannot access this home page outside. The DNS on the company's Internet server resolves the company's home page address to 202.104.137.x (registered IP address). If internal users also use this resolution, the company's home page will not be properly accessed. The solution to this problem is to increase the resolution of the homepage() on the company's internal DNS and point it to 192.168.XX. This configuration is dynamically distributed through the DHCP mechanism so that the client will obtain the specified DNS at the same time when obtaining the IP address. Avoid domain name resolution conflicts.
3.6.3 Browser and Email Tools The original client software is mainly Windows95+office97, including Internetmail, IE3.0 and Outlook97. Due to the low IE3.0 version, it does not support a lot of network interconnection functions, and the speed is slow, so they are all upgraded to IE4.0. The 1E4 packaged Outlook Express is an excellent E-mail tool that is ideal for sending and receiving emails and reading newsgroups. Another option is to use the ready-made Outlook 97, but it is related to Outlook 97 is the client of Exchangeserver (internal mail server), the function is too complicated, huge and slow to start. In order not to influence each other and confuse internal and external mails, Outlookexpress was selected as an independent E-mail tool. After a trial period, users responded well.
At this point, Daya Bay Nuclear Power Plant successfully completed the interconnection of the network and effectively achieved security control. This technology not only positively promotes the production and construction of the existing primary and secondary cores, but also has great promotion value for the future development of three-core and quad-core and the interconnection of other companies.
1.1 LAN Foundation The Daya Bay Nuclear Power Station ("Nuclear") network system has undergone nearly 10 years of construction. It has evolved from a stand-alone microcomputer and a single IBM mainframe system to the current set of mainframes, minicomputers, PC servers, and PCs. Multi-platform, such as a machine, is a network system with network computing as the center and more than 40 application systems running on different platforms. The system covers 18 buildings including the 01th floor, BX building, and BA building within a 5km range. Structured wiring is used inside the connection, and a Category 5 twisted pair cable capable of supporting 155Mbit/s is used. The IBM8271 is used as the endpoint device of the ATM backbone network in each building. It is connected to the 155M backbone network, and 8 or 16 unique 10Mbit/s ports are connected. It can connect to the departmental Ethernet segment, LAN server or IBM8224HUB, under a HUB. There are 16 ports sharing 10 Mbit/s, and 16 workstations can be connected. Two IBM 8260 multi-protocol intelligent switches were placed on the 01th floor and the BX floor, and one RS/6000-41T was equipped with IBM Netview for AIX software as a network management device.
The Ling Ao Nuclear Power Plant (2nd Core), which is 2km away from Daya Bay Nuclear Power Station, also uses ATM technology as a backbone network to build a management computer network. The network uses two BAY5aDOBH and one BAYCl00 as the main switching equipment. BAY28115 and BAYC50 are installed in each wiring room. Through the integrated wiring system of the LBX/LBA building, the user workstation is directly connected or the user workstation is connected through the BAY28113HUB. The network mainly covers the LBX/LBA building, and it also covers some of the office areas on the site and on the 01th floor.
1.2 The issue of networking problems With the continuous development of a nuclear computer application system, computer systems play an increasingly important role in production, maintenance, administration, finance, personnel, etc., CBA (Computer Aided Isolation System), More than 40 applications such as WPMS (Work Process Control System) and AMS (Administrative Management System) are gradually becoming huge productivity resources. With the advancing of the construction of the dual-nuclear engineering project and the beginning of production preparation, a number of application systems, such as the Transfer and Operation Control System (TCS) and the program database system, have become resources that must be shared by one nuclear and two nuclear resources. One or two cores need to run the same software on different servers or directly share the same server and the same software. The amount of information exchanged between the first and second cores is very large. Therefore, the guiding ideology of “one site, multiple reactors, group reactor management,†and “one or two nuclear shared resources†requires that one core and two cores must interconnect computer networks as soon as possible. In addition, the rapid development of the Internet has provided a large and abundant information resource for the production and operation management of the Daya Bay Nuclear Power Station and the construction and management of the Lingao Nuclear Power Station. Whether these resources can be fully and effectively used has become an urgent issue to be resolved. One and two independent LAN systems urgently need to be linked to the Internet.
While the Internet has brought great economic benefits, the importance of network security is particularly prominent. 1. Interconnection between the two core networks requires that the production operation of the single core and the construction of the second core do not interfere with each other, and the interconnection of the nuclear power grid and the Internet requires that the safety of the nuclear power grid itself be guaranteed. Therefore, the interconnection of the first and second nuclear networks and the interconnection between the first and second cores and the international network must address security issues.
2 Networking Schemes 2.1 Analysis of the Interconnection Scheme of the First and Second Core Networks 2.1.1 Networking Principles (1) A core of existing IBM equipment is connected to the newly purchased BAY equipment of the second core. As early as the second core to determine its network program, the issue of the interconnection of the first and second nuclear networks has been proposed. Obviously, if IBM's products are used in the two-core network, the networking is technically very simple. However, considering comprehensive considerations, the two-core network still uses BAY products. Therefore, the work of network interconnection must be based on objective reality. It is necessary to connect IBM equipment and BAY equipment. (2) The network interconnection bandwidth must reach 100 Mbit/s. According to the forecast of the information flow involved in the application system, the network interconnection bandwidth will eventually reach 100 Mbit/s, but the initial bandwidth requirement of the network may be appropriately reduced. (3) After the network is interconnected, the management of division of labor of the first and second nuclear networks. Considering that a nuclear network is mainly used for production and operation, the second-nuclear network is mainly used for engineering construction at this stage. The requirements for security, stability, and real-time of the two networks are not exactly the same, and the first and second nuclear networks are different. Cost centers, financial separation, and equipment management and asset management, separate management are more appropriate. (4) The disruption of a nuclear network cannot be caused during the process of network interconnection. Since a nuclear network is in a real-time production running state, network interruption will have a large impact on production operations. Therefore, a nuclear network cannot be interrupted under normal circumstances. However, in the process of network interconnection, some tests require that the network system must be stopped. In this case, only perfect the plan as much as possible, reduce the number of downtimes, and reduce downtime, especially when making changes to the network, so as to avoid network damage caused by networked tests. (5) Network interconnection with the lowest possible investment. On the basis of ensuring the effective implementation of various functions of the network interconnection, as far as possible, simple solutions and cheap equipment are used to reduce investment costs.
2.1.2 Analysis of major tests (1) Di-nuclear network. Server: The existing server Lanpc-S7, share resources Proj98, configure the corresponding IP, gateway, WINS and other parameters; workstation: Use a laptop, configure the appropriate IP, gateway, WINS and other parameters; Gateway: use 1 SUNNltra1 machine, install the Solaris operating system and Firewall - 1 for Solaris firewall software, set up multiple network cards, configure the appropriate parameters.
(2) Simulation of a nuclear network. Install an NT server LLC, install the WINS service, share the resource test, and configure the corresponding gateway parameters. Workstation: Use a laptop and configure the corresponding IP, gateway, and WINS parameters. The network connection is shown in Figure 1.
On the second-core workstation, first log in to the second-core network with the second-nuclear network ID, Telnet to the firewall, perform user authentication, exit Windows after the login, and log in to the core network with a nuclear network ID, and then map. And use a core of server resources.
On a nuclear workstation, first use a nuclear network ID to log in to a core network, Telnet to the firewall, perform user authentication, and then log out of Windows and log in to the second core network with the second core network ID. Then, the user can be mapped. And use the dual-core server resources.
2.1.3 Basic scheme Similar to the above scheme, through the experimentation and analysis of multi-platform and multi-firewall software, in order to make full use of the resources of one or two cores and save their own investment, and taking into account future functional expansion and development, The one-core network side sets up routers and firewalls, while the two-core network uses the original routing devices and firewalls as peer routers and firewalls, as shown in Figure 2.
2.2 Implementation of the First and Second-Core Network Interconnection Scheme 2.2.1 Server Hardware Configuration SUNU1tra2 Machine: 100M Ethernet port, 2x200MHz CPU, 21-inch display, 256MB RAM, 4GB hard disk, keyboard, 10/100M adaptive Ethernet card; SUNC12for Ultra2/ E2; 3-inch floppy disk drive; tape drive.
2.2.2 server software configuration SUNSolarisServer2.6 Chinese Enterprise Edition; SUNSolsticeFirewall-13.Ob firewall software, unlimited users.
2.2.3 Server Debugging Process The installation and configuration of SUN SolarisServer 2.6 system software; the installation and configuration of SUNSolarisFirewall-13.0b software; the setting of parameters in the application of SUNSolarisFirewall-13.0b; the setting of parameters in the application of SUNSolarisFirewall-13.Ob is divided into three parts: (1) Define Workstation and Network Objects. (2) Create users and groups. (3) establish a rule, the main purpose of the rule is as follows: for any user in a two-core network, allow access to a nuclear network resource (JVC) after verification from a nuclear firewall on any machine of the second-core network. LAN segment); For any user in a nuclear network, any machine from a nuclear network (ie any machine in the JVC-LAN segment) is allowed to pass the verification without a nuclear firewall (but verified by a second-core firewall). ), access to the dual-core network resources; in addition, refusal to exchange visits between any users of the first and second cores and any machines.
2.2.4 Configuration of the Client Side The configuration of the client side of the core; configuration of the Client side of the second core.
2.2.5 Configuration of Static Routes on the Network There are five ELANs configured in the existing one-core ATM network switch, and dynamic routing is adopted between each ELAN. Default Gateway 10.1.3.1 is configured and assigned to the DefaultGateway through the DHCP server. The Client side enables automatic routing and mutual access between machines on the entire network. However, the first and second nuclear network segments are different, and routing problems exist when they are connected. To solve this problem, there are two methods: (1) Manually set static routes on each server and client. This method has a heavy workload, and static routes must be set for each new server or shared resource, which is inconvenient and impractical. (2) Set static routes in the MSS on the ATM network switch. This method Client does not need to change, transparent to the user, but to change the MSS configuration, ATM network switches must be shut down to set; the advantage is transparent to the user, and once and for all. Based on everything for the user, without increasing the workload of the user, making the user easy to use, and being transparent to the user, it is also considered that the change to the MSS configuration is a one-time behavior and does not need to be changed later, so the second method is adopted.
2.2.6 Logging in to the other party's network Steps: Step 1: Log in to the second core network. Step 2: Log in to the second core network.
2.3 Analysis of interconnection schemes between nuclear power grids and international networks 2.3.1 Networking mode selection How enterprises choose the right network access mode and the appropriate ISP according to their own actual situation are the primary issues faced by companies accessing the Internet. Internet access can generally use single-machine dialing, ISDN, ADSL, DDN, etc. The DDN mode is suitable for a certain scale of network systems such as routers, hubs, servers, and workstations, and can be used to publish Web sites, suitable for large-scale enterprises or information services. Business. The original 13 single-line dial-up accounts for the Daya Bay Nuclear Power Station, but the company has hundreds of network users need to access the Internet. Hundreds of stand-alone users access the Internet, which will be very complicated in management. Therefore, from the analysis of transmission rate and cost balance, the management will be very complicated. Therefore, from the analysis of transmission rate and cost balance, consider web publishing and management. The Daya Bay nuclear power plant decided to use the DDN private line method to access the Internet.
2.3.2 Selection of network export points Since Daya Bay Nuclear Power Station is located in Dapeng Town in the outskirts of Shenzhen and is 70km away from the urban area, Renren Exit Point has two options: First, take the Great Wall Tower in the Central District of Shenzhen City as the exit point. The communication line between Great Wall Tower and Daya Bay and the G.703 interface at both ends of the line. The routers were set up in the downtown area and Daya Bay. The network equipment and servers were installed in Daya Bay. Outside the Great Wall Tower, Shenzhen City's Data and Communications Bureau used a special line to pick up Chinanet. Second, take the Dapeng Town Post Office as the exit point, and use Dayeng Bay to use the line of the post office of Dapeng Township to join Chinanet. The previous solution has a high level of network access, is less affected by routing, and has stable lines. It does not require construction. The interface can be reserved with the Guangdong Nuclear Power Group Company located in Shenzhen City. However, the investment for a router needs to be increased, and the workload is relatively large. The latter plan has relatively less workload and simple technology, but it has a low level of network access and is affected greatly by routes. The Dapeng branch has a relatively low level of technical and service personnel, and the line is unstable. Construction problems may exist. Through the above-mentioned advantages and disadvantages, Daya Bay Nuclear Power Station chose Great Wall Building as the exit point of the Internet special line.
2.3.3 Firewall Selection Effectively protect the internal network security of the company and allow internal users to efficiently access the Internet resources. This is a standard requirement of the firewall. When choosing, there are three factors to consider: safety, stability, and high performance.
As far as Cisco PIX Firewall is concerned, it is a hardware-based dedicated firewall that effectively hides internal network addresses. It only has one or several virtual addresses externally, and true hosts and users do NAT (Network Address Translation) or PAT. (Port address translation), completely hidden, with high security. In addition, the control microcode used by the PIX is different from the source code of the software firewall and is not easily available to hackers, thereby further improving the security. PIXFirewall's security algorithms are also special. CPU-based firewalls based on Unix or other operating systems process a large number of packets at the application layer. PIXFirewall uses secure real-time embedded systems at the network level and below. Process the data.
PIX's high performance also benefits from its pass-through proxy feature. Once external access is verified to meet the requirements of the control system, it converts the conversation flow so that the traffic flows directly between the two parties. This speeds up the operation and greatly reduces the number of ordinary firewalls. The amount of resources spent on user authentication. Due to the hardware-based architecture, the execution speed is extremely fast and throughput is high. At full load, the operating speed exceeds 45 Mbit/s, supports T3 speed, and can support up to 16000 TCP sessions at the same time. This performance is based on Unix firewalls. Several times. Simple configuration management is also a highlight of the PIX. Once configured, it does not require frequent maintenance. In this system, 3 network card configurations are used to enhance security and flexibility. The WebServer and MailServer that are traditionally placed on an external network are also placed under the protection of the Firewall (ie, the DMZ zone), leaving ample room for security for future high-security applications such as e-commerce applications. Therefore, Daya Bay Nuclear Power Station chose the hardware firewall PIXFirewall as the Internet firewall.
2.3.4 Server Selection The server is the core of the system. Whether the server hardware and software can be correctly selected and successfully installed is the basis for the success of the entire system; whether or not they can be effectively used after successfully installing the server hardware and software is the guarantee of the system operating efficiency. . The choice of server generally considers reliability, security, and processing power. With regard to the specific choice of servers, four sets of solutions have been designed, as listed in Table 1 below. In the above 4 sets of solutions, the solution of SUN server plus Cisco PIXFirewall has many advantages. The combination of SUNUltra hardware platform and Netra Internet software is a solution specifically designed to solve the Intemet networking problem. This solution has stronger functions in terms of hardware structure, reliability, scalability, and is applicable to larger enterprises. Therefore, in the selection of servers, the SUNAtra server is used in the Daya Bay nuclear power plant Intemet system.
2.3.5 Client hardware and software selection The hardware directly utilizes various types of PCs already on the Daya Bay nuclear power plant network. The client software also directly utilizes the existing Chinese Windows 95. This will save investment on the one hand and the other on the other. Department users can use Intemet on the basis of the original software and hardware, reducing the workload of user training and software installation, and users will feel simple and easy to use.

2.3.6 Router Selection There are two routers in the Internet access line of Daya Bay Nuclear Power Station, namely No. 16 Building of Great Wall Tower in Shenzhen and 01th Floor of Daya Bay Nuclear Power Station. Combined with the existing network conditions of Daya Bay Nuclear Power Station, there are two types of routers to choose from, one is the IBM2210 router and the other is the Cisc04500 router. Other brands and models of routers have no special advantages. In comparison, IBM2210 and Cisco4500 have a wider range of features and options, are cheaper, and have a higher utilization rate in Internet node connections, facilitating technical support. In particular, the Cisc04500 system software image is compressed and stored in flash memory. Memory is more reliable than disk and is easy to develop and maintain. Therefore, Cisc04500 was selected in the Internet access plan of Daya Bay Nuclear Power Station.
2.4 Interconnection Scheme of Nuclear Power Grid and International Network Implementation 2.4.1 Basic functions Establish a 128K DDN dedicated line and connect the Internet system of the nuclear power plant to the Chinanet backbone network through a dedicated line. This DDN private line supports most of the protocols based on Internet. The standard Internet service for internal users, including Web browsing, FTP, Telnet, and E-mail services based on POP3/SMTP. Open the company's Web site to external users. The system can also provide BBS, directory services, etc. With the deepening of Internet applications, new services will be added to the system.
2.4.2 System Configuration Functions (1) SUN server. Configuration: SunUltra10Server, CPU300MHzUltraSvarc, hard disk 4.3G, 128M memory, 24xCDROM, 1.44M, floppy drive, 10M/100MEthernet network card, 512KCache, based on Solaris2.6 Chinese operating system, running Netral3.2 groupware; function: WebServer is Netra13.2 group Bundled Netscape Enterprise Server 3.0; E-mail service: provided by Sendmail, is a built-in component of the operating system; DNS service: BIND, is an international popular Unix-based universal freeware; BBS service: shareware, downloaded from Internet.
(2) Backup DNS server. Configuration: 1 PCServer based on NTServer4.0; Function: As a backup of the primary DNS, it works in the case of a failure of the primary DNS (such as a down machine) to resolve the company's domain name.
(3) Proxy server. Configuration: PCServer, dual SCSI hard disk, based on NTServer4.0, running MSProxyServer2.0; features: (0 as a proxy for users to access the Internet, including WebProxy and WinsockProxy, where WebProxy implements HTYP, n7, Gopher, SSL, and other browser protocols, and With the local cache Cache configured, Winsock Proxy opens other protocols, including the POP3/SMTP mail protocol, acting as a proxy for the post office so that Winsock clients can communicate transparently with the mail server.2 User Management: Proxy Server is responsible for user authentication, traffic Monitoring, user accounting and other management tasks.
(4) PIXFirewall. Configuration: Cisco's professional hardware firewall, with three 10/100M adaptive Ethernet cards, 1024 simultaneous session licenses, configuration information is written to the built-in FlashMemory; Features: PIXFirewall firewall provides network-level security protection as The system separates the security gateways of the internal and external networks and the DMZ (public security zone) network segment, and hides the internal network through address mapping to prevent hackers from attacking the intranet. Configure the necessary protocol pipes (WWW, DNS, etc.) for external users.
(5) Router. Configuration: 2 Cisco 4500 modular routers, one of which is equipped with a 4-port G. 703 modules and one dual serial port module, and another one is equipped with a 4-port G. 703 modules and a dual Ethernet module; Function: Cisc04500 is Cisco's high-end products that support E1 (T1) line connections. In this system, in addition to the standard network route, the router 4500 has one important application: using G. The 703 module realizes 2M bandwidth communication between Shenzhen Great Wall Tower and Daya Bay, and can achieve hot backup of fiber/microwave communication.
(6) DTU. The NewBridge2603 synchronous data transmission unit is connected to the DDN network node at the opposite end of the data post office to realize synchronous communication of Internet information data.
(7) Hub. 3comOfficeConneet intelligent hub, light and simple, used for network segment expansion and device-to-terminal signal relay.
2.5 Security Strategies for Nuclear Power Networks 2.5.1 One- and two-core networks use mutual authorization control between firewalls to limit human-to-human interactions on the one hand; on the other hand, they also control technical factors such as broadcast storms on networks. influences.
2.5.2 There is no direct channel from the external network to the intranet. There are firewall and ProxyServer 2 barriers, and external users cannot access any resources on the intranet.
2.5.3 From the external network to the DMZ Subnet The firewall (PIX/Firewall) is required. It is the only network segment accessible to external users. The company's Internet host, SunServer, is on the DMZ subnet. The firewall performs strict security settings: the DMZ subnet uses the reservation IP address of the Internet, and an address mapping pipe is established between the external network and the DMZ. The external user accesses only the mapped IP address of the host on the DMZ, and does not know the real IP address. Can not be directly accessed, thus achieving IP address translation and shielding, effectively preventing IP fraud and other hackers commonly used tactics.
2.5.4 There are two barriers from the DMZ to the intranet with firewalls and proxy gateways. There is no direct pipeline.
2.5.6 From the Internal Network to the Extranet Through the PIX/Firewall/proxy, you can transparently access Internet resources (connected to the opened service). After proper configuration of the gateway and the PIX, various external access services can be carefully adjusted, all IP packets can be filtered, and all access information can be monitored.
2.5.7 From the Internal Network to the DMZ
Open protocols such as HTTP, Telnet, and POP allow authorized users to access this network segment transparently.
2.5.8 From the DMZ to the external network Through the firewall, the external network can be transparently accessed.
The above strategies are mainly set for the direct invasion of external hackers, but hackers can also use indirect means to attack, mainly: mail delivery and internal users to download infected files, which is already within the scope of the virus. Currently on the intranet, with the exception of Unix hosts, software for real-time monitoring of viruses (Cheyenne AntiVirus for CA) can effectively monitor the delivery and execution of files. In theory, it can prevent the spread of infected files. With the development of network technologies, the security strategy of nuclear power networks is also constantly improving. Connection between different ATMs in a two-core backbone network Although ATM technology has developed over the past few years, its stability, security, and manageability have been strong, but there are still problems with complex architecture and inconsistent agreements among vendors. Difficulty in connecting ATMs from IBM to BAY.
3.2 First and second nucleuses 2 Different management methods of the network One nuclear network is mainly used for production and operation. The second-nuclear network is mainly used for engineering construction at this stage. The one-nuclear network covers a wide range, except for the production system, finance, personnel, Management systems, such as labor and capital management, are also running on it. The two networks have very different management methods, such as networking methods, network segmentation, and virtual network settings, which create difficulties for network interconnection.
3.3 Networking process Experimental conditions Difficulties A nuclear network is in operation and cannot be interrupted. A dual-core network does not have a complete physical environment, and networked devices cannot be purchased before the actual solution is determined. Therefore, they must be simulated first. Conduct networking experiments and make theoretical projections, then research, select, determine networking solutions, and purchase related equipment. This kind of process is more difficult and risky for the initial experiment.
3.4 Long-distance communication between nuclear power grid and international network In this system, the access point of the Internet is in the Great Wall Building of Shenzhen City, and the servers and company users are all in Daya Bay, and the distance between them is 70km. How to reliably cross this distance and effectively transmit information is a challenging issue. The system uses two Cisco 4500 routers as the end devices, using fiber optics and microwave access to solve this problem.
The Cisco 4500 is a modular router that integrates 4 2M (E1) ports on its standard G.703 module and provides up to 8M of bandwidth at the same time. Connecting two E1 lines can be set as hot backup. When one channel fails, it can be automatically switched to the other. When there is no fault, two E1 lines are transmitted concurrently. This feature is used to achieve hot backup of the fiber/microwave. In communication debugging, the initial discovery error rate is as high as 40%. After searching for reasons by multiple parties, after resetting the Timeout value and related parameters, the code rate is reduced to a few PPM (parts per million), and the transmission quality is better than Intemet signal quality requirements for transmission channels.
3.5 Nuclear Power Grid User Management and WebCache (Cache)
3.5.1 Stable and reliable user authentication, logging, and traffic statistics are important aspects of network management. Initially, PIX-based ACS authentication was used, but failed to achieve the desired goal. Later, it adopted a proxy server and carefully configured it. Performance adjustment satisfactorily solved the complex requirements put forward for network management and achieved: (1) stable security verification, user authorization, and resolution of the problem of unified coordination with the main domain of the company's internal network, ie, one login, one verification, and transparency Use authorized services. (2) More detailed monitoring functions, including system performance monitor and real-time user status monitoring. (3) User log, log content includes: user ID, login time, information flow, service type, access to resources, etc., and can lead to a database for easy management.
3.5.2 Establishing a Local Cache is the Key to Improving User Response Performance After implementing user management with Proxy, Proxy Cache is also used to increase the Proxy's corresponding hard disk space. It can actively and periodically cache files that users have accessed to ensure the availability of data. Through Cache, the control over network resources has been greatly improved, the congestion of exported Internet has been reduced, and expensive information fees have also been saved. In fact, the speed of Internet access by internal users depends largely on the performance of the high-speed cache.
3.6 Client Configuration 3.6.1 About defaultgateway The company intranet has multiple subnets: 10.1.xx, 10.2.xx, 10.3.xx, etc. To enable users of different network segments to achieve smooth resource sharing, you must set The correct defaultgateway. In the initial implementation of the solution, the PIX internal Ethernet interface company 10.1.XX network segment, the user to access the Internet through the PIX, the default gateway must point to the PIX's internal Ethernet interface, but users of other network segments will not be able to access the Internet. To do this, first set up a static route on the IBM 8260 Switch (smart switch on the backbone) and point the Internet gateway to this PIX port. However, it has a great impact on the stable operation of the company's backbone network, and some of the company's online applications are 24 hours without interruption. Therefore, it adopts a proxy service mode to set up a proxy gateway at the user's end to ensure no change to the existing intranet. Next, this routing problem is better implemented.
3.6.2 Internal User Access to the Corporate External Home Page The corporate home page is located on the DMZ network segment (1P: 192.168.xx) and is independent of the external Internet and intranet. Internal users cannot access this home page outside. The DNS on the company's Internet server resolves the company's home page address to 202.104.137.x (registered IP address). If internal users also use this resolution, the company's home page will not be properly accessed. The solution to this problem is to increase the resolution of the homepage() on the company's internal DNS and point it to 192.168.XX. This configuration is dynamically distributed through the DHCP mechanism so that the client will obtain the specified DNS at the same time when obtaining the IP address. Avoid domain name resolution conflicts.
3.6.3 Browser and Email Tools The original client software is mainly Windows95+office97, including Internetmail, IE3.0 and Outlook97. Due to the low IE3.0 version, it does not support a lot of network interconnection functions, and the speed is slow, so they are all upgraded to IE4.0. The 1E4 packaged Outlook Express is an excellent E-mail tool that is ideal for sending and receiving emails and reading newsgroups. Another option is to use the ready-made Outlook 97, but it is related to Outlook 97 is the client of Exchangeserver (internal mail server), the function is too complicated, huge and slow to start. In order not to influence each other and confuse internal and external mails, Outlookexpress was selected as an independent E-mail tool. After a trial period, users responded well.
At this point, Daya Bay Nuclear Power Plant successfully completed the interconnection of the network and effectively achieved security control. This technology not only positively promotes the production and construction of the existing primary and secondary cores, but also has great promotion value for the future development of three-core and quad-core and the interconnection of other companies.
180 elbow,plastic elbows,elbow plastic mould,injection moulded elbow,elbow injection mould,elbow plastic mold
Dongguan Hongke Plastic Precision Mould Co.,Limited , https://www.hongkemold.com